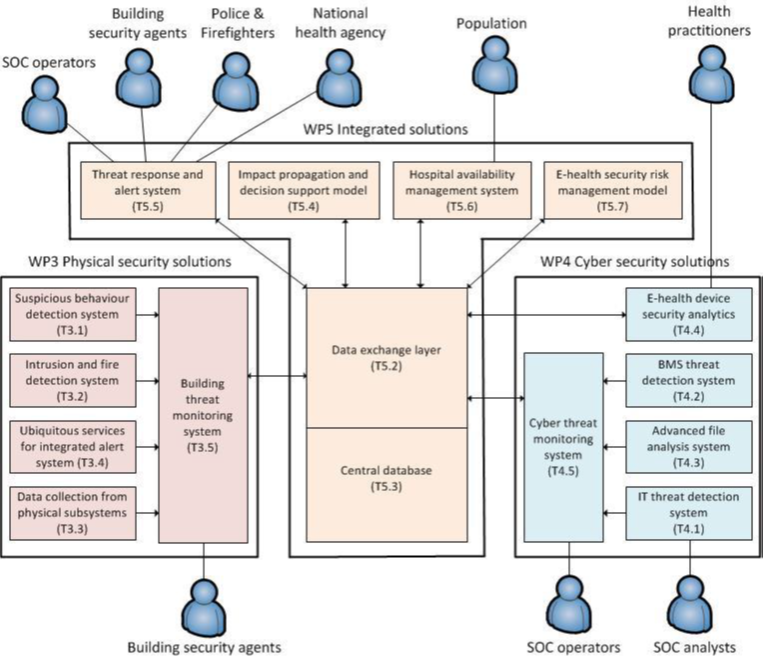
A combination of the innovation elements explained below will bring a significant improvement in protecting critical health infrastructures.
Description: The suspicious behaviour detection system will capture video streams from surveillance cameras. It will perform near real-time analysis and it will trigger security alerts in case of crowding, loitering in restricted areas and suspicious activities on integrated devices. Validation of emergency situations will be improved by automated approaches to cross-correlate events from the suspicious behaviour detection system with information from other sub-systems.
Excellence: The system will analyse video streams using improved pattern detection techniques to generate metadata. Video analysis will use object detection and classification techniques combined with expected behaviour modelling and efficient image transformation techniques. If relevant, the system will also use metadata directly coming from the cameras. One of the main challenges will be to process a huge quantity of data in near-real time. It will be necessary to optimize hardware and software architecture keeping under consideration cost-effectivity of the final solution.
Description: Even today, physical intrusions resulting in theft, tampering or break-ins are an important vector of threats for critical infrastructures. Fire is also a preeminent risk that cannot be underestimated. By interconnecting the video monitoring system with existing access management and fire detection systems, it will be possible to notably extend threat detection capacities and reduce number of false positive incidents.
The video monitoring system will learn to recognise intrusion and fire start. Linking events to relevant video streams will improve verification and handling of intrusion and fire alarms thereby reducing false positive detections and in turn increase the efficiency of security personnel.
Excellence: The excellence of this element relies on several components:
(1) A communication layer between different standard protocols in different domains;
(2) Advanced techniques for video recognition of abnormal access, flame and smoke;
(3) Threat detection models that will combine video events with other security events coming from access management and fire detection systems.
Description: It aims at informing key personnel of a suspicious activity in the hospital and reducing latency times for intervention. The mobile appliance allows the building security agent to be informed and alerted when he is doing a check round whereas the building monitoring systems is only accessible from the control room.
Excellence: The novelty and excellence of this component is represented by its interoperability with the project ecosystem and the encompassing approach to physical threats, cyber threats and related impacts. A high level of attention will be granted to system scalability and adaptability in existing facilities. Being validated by end users, assuring on-the-field large scale tests in multiple stressful situations, it will represent a valid candidate to be taken into consideration by standardization bodies, when defining the guidelines for critical infrastructures, with respect to physical security.
Description: The building monitoring system will centralise security events from the suspicious behaviour detection system, intrusion and fire detection system, access management system, air cooling system, power supply system. It will allow building security agents to monitor physical assets on a building representation and it will give access to the video streams. The building monitoring system will also have the ability: to report security events on physical assets; to manage manual acknowledgement of security events; to forward acknowledged incidents to the central database; to set rules based on related impacts coming from the central database; to trigger response and mitigation plans with regards to the impacts.
Excellence: Such an integrated and automated system will result in operational savings, due to energy savings, lowering manual resource costs and improving ease of use through integrated security monitoring and intelligent response. Developing this innovation element will require a huge technological effort in order to embed real-time data streams (including video) on client-server architectures.
Description: The IT threat detection system captures the network traffic and performs near-real time analysis in order to detect suspicious behaviour and scale up security events to the cyber threat monitoring system.
Excellence: The IT threat detection system will use a hybrid approach combining both non-supervised methods and supervised methods in order to improve threat investigation and threat detection on the network traffic. Nonsupervised methods will be improved to enhance cyber threat detection and to limit the number of false positive and false negative events. Non-supervised methods are based on threat pattern matching in near real-time. In addition to usual methods provided by IDS systems, the IT threat detection system will embed new detection capabilities relying on metadata extracted from the network traffic. Metadata will be used to perform timeline analysis and identify abnormal behaviour on the network. Supervised methods will be studied in order to improve investigation capabilities on new attacks, also known as 0-day attacks, which cannot be detected with threat pattern matching methods since new threats are not already referenced in the malware databases. Machine learning algorithms will be trained to automatically classify data extracting suspicious network traffic and therefore simplify threat pattern investigation by SOC analysts. Relying on a virtuous and incremental approach, supervised methods will allow SOC analysts to identify new threat patterns, update the malware database and therefore, improve threat detection at SOC operator level.
Description: The system will increase security protection and situational awareness by passively monitoring network traffic between the building management system (BMS) and the building control sub-systems (e.g., lighting, power, medical devices, lift). The BMS passive probe will perform in-depth protocol parsing of the most commonly used protocols (e.g., BACnet, LonWorks) in order to detect specific threats and 0-days attacks to building automation systems.
Excellence: The BMS probe will improve the state-of-art in building automation networks in the following ways:
(1) An automatic asset inventory for the identification and characterization of devices that comprise a building automation network. In networks that include hundreds of devices, organized in tens of sub networks, maintaining situational awareness by manual inspection becomes unfeasible. As such, the operators of these networks can find great benefits from the automatic extraction of network information in order to have a coherent and up-to-date picture of the components entering and leaving their network. In addition, asset information can be used to help threat detection by providing contextual and semantic data useful to e.g., rank alerts according to the criticality or the vulnerabilities of certain assets.
(2) A building automation threat hunting to detect intrusions by considering indicators of compromise that hint to the presence of cyber-attacks targeting building automation. Examples of indicators of compromise include unusual numbers of message types (e.g., too many I-am-router or too many Whois messages), unusual services or port numbers or unusual communication patterns (e.g. connection going from controllers to the Internet).
(3) An anomaly-based intrusion detection system to detect 0-days and targeted attacks. In this solution, a normal baseline is built by observing network behaviour and by profiling network devices in terms of message sent or received, objects properties and communication patterns. Techniques such as unsupervised learning and histogram-based machine learning techniques will be adopted to build device profiles. In case a deviation from a profile is identified, an alert (possibly enriched with contextual and semantic information coming from the asset inventory) will be raised.
Description: The advanced file analysis system is basically connected to different kind of equipment: probes, firewall, SIEM, third party services. The detection of malicious files relies on different approaches: static analysis such as signature matching, heuristic analysis and dynamic analysis. Signature matching is a determinist method only effective if the malware is already known. Heuristic methods are able to identify several variants of a virus but can generate false-positive events. Dynamic analysis consists in “running” the file in a suitable environment in order to highlight suspicious behaviours. First, the system performs static and heuristic analyses to detect malicious code in the file. Then, it put files in a sandbox environment to perform a dynamic analysis. It studies suspicious behaviours such as unexpected queries and external connections in the simulated environment. Finally, the system provides a report including a threat assessment.
Excellence: Most available tools only perform static approaches and only deal with common Office file formats. The advanced file analysis system will be improved in order to take into account health related file formats currently exchanged in health infrastructures. A deep study of each format will be performed to identify how it can be used as a vector of threat. According to the study, static and heuristic analysers will be updated to detect such potential vectors. In parallel, the dynamic analyser will be updated in order to observe these types of file in a suitable environment and identify suspicious behaviour. According to the dynamic analysis, the advanced file analysis system will be able to define a threat pattern that could be added to malware database. New connectors will be implemented with the equipment provided by the project (IT probes, BMS probes) but also by introducing real solutions in the demonstration sites (firewalls). The advanced file analysis system will not only improve detection capacities on the probes, but also response capacities on active equipment such as firewalls. It will not only improve the security of external exchanges by reinforcing the security policy on the firewall, but also internal threat detection on the probes. Security policy at a firewall level could take into account the result of file analysis before applying an appropriate reaction such as raising a security events or dropping the file.
Description: The e-health device analytics solution collects data from medical devices, combines it with other (public) data sources and performs analytics to derive meaningful security data to help identify, assess and manage threats and risks affecting the e-health devices.
Excellence: The e-health device analytics solution innovates through its data-driven approach that leverages data directly from the medical device and its environment. Traditionally, the security of medical devices relies on expert judgment on risk, security-by-design, incident response, etc. Also, devices are typically not specifically programmed to log and report their own security state and their environment. Novel aspects of the solution include leveraging the existing support infrastructure such as device logs and complaint management systems to identify meaningful security attributes and risk indicators through advanced analytics. This method is further improved by programming devices with specific extensions. Consequently, the e-health device analytics solution improves upon state-of-the-art solution by being data and model driven and by providing insights over the device (long) life cycle in a changing security environment, which leads to better threat and risk management.
Description: The cyber threat monitoring system collects cyber security events from multiple security assets: probes, IDS, IPS, SIEM, firewall. It mainly focuses on threat detection and incident response along the crisis lifespan.
Excellence: The cyber threat monitoring system centralizes cybersecurity events on a unique dashboard dedicated to SOC operators. Relying on the impact propagation model, the system will display potential cascading effects in case of security incidents. It will provide a global picture of physical and cyber impacts to the SOC operators. The dashboard will also improve investigation capacities by displaying relationships between “impacted” equipment and “monitoring” equipment. Therefore, it will simplify evidence retrieval. Being aware of potential impacts, an SOC operator will better understand the emergency level and will be in position to make better decisions, improve incident response and mitigate the impacts. The cyber threat monitoring system will increase SOC operator awareness and will support decision making by proposing an appropriate response plan to solve the incident and mitigate the aftermaths. The cyber monitoring system will include a user-friendly interface and will embed a graph-based representation of interconnections between critical assets.
Description: The use of a database will allow partners to centralize and share data coming from the different physical and cybersecurity systems. A flexible platform will be used to manage different kind of databases that can be column oriented or file oriented, different types of data and different file formats. The database will allow partners to send real time requests to quickly send and retrieve relevant data, in rapid elapsed times, near real time acquisition and processing.
Excellence: The database and data exchange layer will be designed to standardize data exchange between the different project bricks. Incidents stored in the database will be previously validated by security operators (building security agents or SOC operators), thus reducing the amount of false positive alerts. By implementing standardized data models, by implementing relevant processes (correlation between incidents, impacts and responses), the central database will return relevant data and optimize decision support. Furthermore, work on the standardized exchange layer will pave the way for interconnected health services to improve security and defence strategies at national and European level. The analysis and comparison of individual scenarios, in three different European sites, will provide additional information about the behaviour of different environments in healthcare structures across Europe. Information coming from the three scenarios evaluation, via the platform, will allow security staff to positively impact the security of their facilities and, above all, the people in their care.
Description: The impact propagation model formalizes the relations between physical and cyber assets and threats in health services with a view to simulating cascading effects propagation between these assets. Based on this model, it will be possible to anticipate the potential impacts of cyber and physical incidents, not only on building infrastructures (power supply, air cooling, etcetera), but also on IT systems and medical devices. Beyond the technological impact the model will also take into account impacts on patient security and safety.
Excellence: The impact propagation model is based on an ontology that describes critical assets based on a risk analysis as well as relations between physical measures from sensors, process information from the Cyber threat monitoring system and the e-Health devices security analytics tool. Hence, the ontology will interconnect the physical concepts (e.g. hardware devices) to the cyber concepts (e.g. data and services). The description of each concept will include information such as name, type, reference, location, operational status, etc. It will also include the impact of a threat on a given concept and on concepts connected by hierarchical and non-hierarchical relations in the ontology.
In addition, rules (e.g. SWRL rules) can be added to the ontology to express complex knowledge and provide more inference possibilities. The impact will be inferred from the ontology axioms and rules using reasoners (e.g. HermiT).
Thus, by identifying the cascading effects it will be possible to evaluate the real or potential impacts of an attack on a component on other components, to identify precursor events and next critical scenarios. The impact propagation model will allow SOC operators and building security agents to make better decisions, improve incident response and mitigate the impacts. More concretely, a web service interface (based on the ontology, rules and reasoner such as HermiT) will be implemented that input incidents, and infer, in a near-real-time, impact and relevant monitoring devices.
Description: The alert system is on standby and awaiting incoming signals to trigger pre-configured workflow, implementing the multi-step processes. It combines the ability to deliver notifications, alerts and mobilize resources based on the incoming event.
Excellence: There are no off-the-shelf software solutions combining multi-channel notification delivery systems, implementing notifications, alerts, and notification and mobilization functions along with a process/workflow engine. SAFECARE aims to implement both in a single solution that allows users to project their organisation’s process in case of an alert, so as to deliver mass alerts, pre-alerts on specific skill-based group, mobilize given groups or mobilize a given skill-group and stop when a quorum is reached. It allows a relatively accurate, fast and reliable way to ensure that the right people get the right message and to-do action.
The platform consists in a real-time multi-channel notification and alerting system, ‘spawning’ a given workflow instance based on the triggering input data that continuously executes each block of the process. Workflow logic includes communication tasks as well as purely workflow related task such as conditional switch, wait / join / fork tasks, evaluation blocks, etcetera. The platform will be integrated with any software through its API, hence extending its ability to alert and organize a response team in a streamlined, fast, multi-channel fashion. All process execution issues a fully-detailed report that users can rely on to measure key performance indicators (KPIs), learn and improve. It is therefore required that the processes designed for each event can be evaluated with at least one KPI.
Description: The Hospital Availability Management System (HAMS) will allow medical and healthcare organizations to share status and availability information with each other and with the population. It is based on a web application to periodically report hospital availability, allowing the population and emergency teams (firefighters, red cross, etcetera) to immediately find the closest hospital that can provide the needed health services.
Excellence: When a physical threat interrupts the normal operations of a hospital, there is a need to communicate with other hospitals, and to quickly gather data with regard to hospitals’ bed availability, status, services, and capacity.
This would allow emergency dispatchers and managers to make sound logistical decisions about where to route people and which hospitals can provide required services. Systems currently used by hospitals were developed following different interfaces and data formats; therefore they are not able to properly communicate with each other.
The proposed HAMS aims at overcoming such issues of communication interoperability. It is based on the Emergency Data Exchange Language -Hospital AVailability Exchange (EDXL-HAVE) standard defined by OASIS Emergency Management technical committee. Since EDXL-HAVE has a relatively comprehensive data model, the main functionality of HAMS is to provide an easy way for hospitals to exchange information through the aforementioned standard. The adoption of EDXL-HAVE data format is aimed at enhancing the overall health service resilience through a more efficient coordination of different hospitals. In particular, from the information management perspective, the use of the HAMS favours interoperability among healthcare organization and flexibility as it can be adapted to share data for different kinds of health services. The advantages of HAMS will be particularly useful to cope with unexpected interruptions of hospital operations. Indeed, thanks to fast and clear information exchange, other nearby hospitals will be able to communicate their availabilities to host additional patients and to provide specific health services.
